
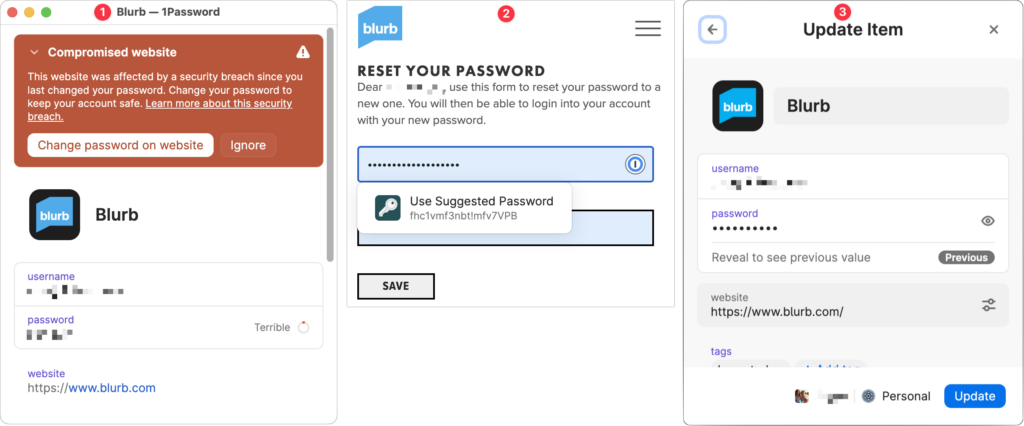
January’s big security news was the Mother of All Breaches, the release of a massive database containing 26 billion records built from previous breaches across numerous websites, including Adobe, Dropbox, LinkedIn, and Twitter. It’s unclear how much of the leaked data is new, but it’s a good reminder to update your passwords for accounts on compromised sites, especially those you reused on another site. Cybernews has a leak checker that reports which breached sites include your data. More generally, password managers often have a feature that checks your passwords against the Have I Been Pwned database of breaches and helps you change compromised passwords—1Password’s is called Watchtower, shown below. You can also search Have I Been Pwned directly. Don’t panic if your email address appears in numerous breaches because some of the theoretically compromised accounts may be defunct sites, trivial sites you used once 10 years ago, or duplicate password manager entries for a site whose password you already updated.
(Featured image by iStock.com/Prae_Studio)
Social Media: Worried about the “Mother of All Breaches” that has been making the rounds in security news? We share a leak checker that can tell you if your email address was involved and recommend that you update any compromised passwords.








